Certificate Authorities revoking non-compliant certificates, potentially impacting your App Service
If you have received a notification from Azure about potentially being impacted by the certificate revocation issue, follow these steps to avoid application interruption.
Certificate Authority (CA) Browser forum recently published reports of multiple certificates issued by CA vendors that are used by our customers, Microsoft, and the greater technology community that were out-of-compliance with industry standards for publicly trusted CAs. The reports regarding the non-compliant CAs can be found here:
As per the industry’s compliance requirements, CA vendors began revoking non-compliant CAs and issuing compliant CAs. This requires customers to have their certificates re-issued. Microsoft is partnering closely with these vendors to minimize the potential impact to Azure Services. However, your self-issued certificates or certificates used with “Bring Your Own Certificate” (BYOC) are still at risk of being unexpectedly revoked.
If you have been notified about using a self-acquired certificate or using the BYOC feature on App Service that is potentially impacted by this issue, check if certificates utilized by your application have been revoked by referencing DigiCert’s Announcement and the Certificate Revocation Tracker. New certificates need to be requested from the CA vendor utilized in your applications.
NOTE: This issue will not affect App Service Managed Certificates
Avoiding Application Interruptions
To avoid your application’s availability being interrupted due to certificates being unexpectedly revoked, or to update a certificate which has been revoked, follow the steps below:
- Reissue your certificate (contact your certificate provider for more information).
- Once your new certificate has been reissued, add the new certificate to your web app by either uploading the new certificate to your web app or by updating the new certificate in your Key Vault
- Once you have added your certificate to your web app, you will need to update your bindings refer to the next section.
How to safely update your bindings
Certificate Imported from Key Vault to App Service
If you are importing your certificate from Key Vault, App Service has a background job that will automatically update your bindings with the new version of your certificate within 48 hours.
If you’re using Key Vault and you would like to immediately update your bindings and not wait for the background job, follow these steps below:
NOTE: If you are using IP SSL bindings – *do not delete* your bindings as your inbound IP can change. It is recommended to wait for the platform’s background job to update the bindings with the new version of your certificate to avoid losing your IP address.
- Upload the new certificate in Key Vault using a new certificate name
- Import the new certificate to your web app
- Update your binding
- Delete the old certificate from App Service
Certificate Uploaded to App Service
If you are uploading a certificate to your app web, you will need to update the bindings with your new certificate following the steps below:
Note: If you are using IP SSL bindings – *do not delete* your bindings as your IP inbound IP can change. Instead you must only *update* the IP SSL bindings.
- Upload the new certificate to your web app
- Update your binding
- Delete the old certificate from App Service
Updating bindings
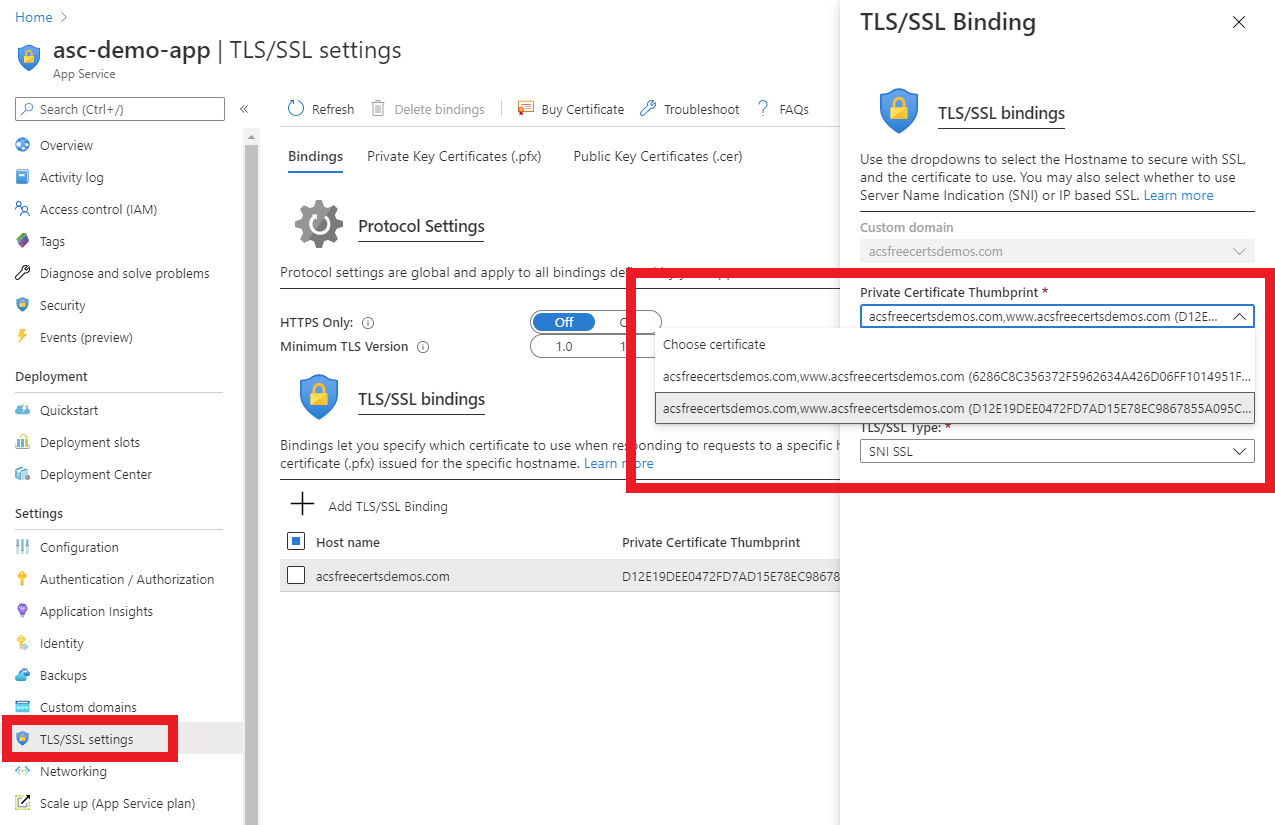
Through Azure Portal
On Azure portal, go to “TLS/SSL settings” under “Settings” on the left navigation of your resource, select the binding you would like to update, and look for the new certificate from the dropdown.
Through Scripts
- Refer to the documentation on sample scripts for Azure CLI and Powershell
- Note: You can run “New-AzWebAppSSLBinding” to add the new certificate to the existing hostname
- Refer to the blog to rotate you certificates with Key Vault using ARM
