Appendix¶
This section has additional information that might be needed for vFXT cluster configurations.
Click a link to jump to the following sections:
- Required ports
- Domain whitelist
- Creating AWS S3 endpoints
- Multiple availability zone (Multi-AZ) support
- Customizing the cluster node role
- Sample IAM policy
Required ports¶
The ports listed in this section are used for vFXT inbound and outbound communication.
Never expose the vFXT or the cluster controller instance directly to the public internet.
NFS¶
| Inbound and Outbound | ||
|---|---|---|
| TCP/UDP | 111 | RPCBIND |
| TCP/UDP | 2049 | NFS |
| TCP/UDP | 4045 | NLOCKMGR |
| TCP/UDP | 4046 | MOUNTD |
| TCP/UDP | 4047 | STATUS |
SMB/CIFS¶
| Inbound | ||
|---|---|---|
| TCP | 445 | SMB |
| TCP | 139 | SMB |
| UDP | 137 | NETBIOS |
| UDP | 138 | NETBIOS |
| Outbound | ||
|---|---|---|
| TCP/UDP | 53 | DNS |
| TCP/UDP | 389 | LDAP |
| TCP | 686 | LDAPS |
| TCP/UDP | 88 | Kerberos |
| UDP | 123 | NTP |
| TCP | 445 | SMB |
| TCP | 139 | SMB |
| UDP | 137 | NetBIOS |
| UDP | 138 | NetBIOS |
Domain whitelist¶
Make sure that these web URLs are accessible from your cluster.
You will also want to whitelist the AWS S3 and EC2 endpoints used by your instances. Refer to these documents for specifics:
https://docs.aws.amazon.com/general/latest/gr/rande.html#s3_region
https://docs.aws.amazon.com/general/latest/gr/rande.html#ec2_region
Creating AWS S3 endpoints¶
If using AWS S3 for storage as a core filer, you should enable S3 endpoints, which allows S3 traffic to pass through a customized gateway instead of using the public gateway to your VPC. This access strategy optimizes throughput for S3 traffic, making your storage system more available.
Use the AWS console to create an endpoint:
- Navigate to the VPC service within AWS.
- Click Endpoints on the left.
- Click the blue Create Endpoint button at the top.
- Choose the VPC, service, and policy.
- Click the blue Next Step button in the lower right.
- Click the checkbox next to the private route table used by the vFXT cluster.
- Click the blue Create Endpoint button in the lower right.
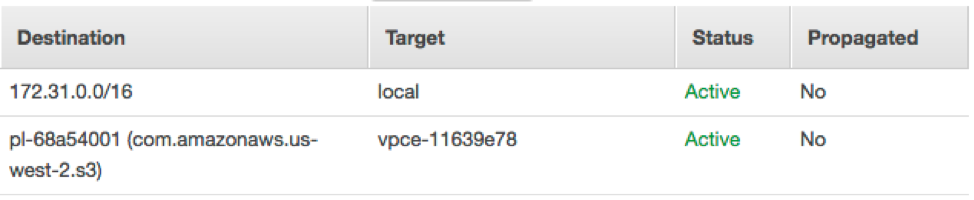
To verify that the endpoint was correctly created and applied to the route table:
- Navigate to Route Tables within the VPC service console.
- Click the route table at the top.
- Click the Routes tab at the bottom.
- Verify that there is a route at the bottom that begins with “pl.”
Multiple availability zone (Multi-AZ) support¶
The recommended Avere vFXT cluster configuration is to have all nodes running within a single AWS Availability Zone (AZ). This arrangement provides the best performance and lowest cost.
For more information, see the AWS Availability Zones documentation.
For disaster recovery scenarios, the vFXT cluster can support nodes in multiple AZs. This configuration increases latency and costs as node data is transferred across AZs within the same region. It allows a node in one zone to take over serving requests from a node in a zone that has gone down. The operating vFXTs reprogram routes and allow clients to connect to the same IP address used on the failed vFXT.
You can create a Multi-AZ cluster that has one node in each of three different availability zones. This is the only supported configuration.
Multi-AZ requirements and restrictions¶
To use a Multi-AZ configuration, administrators must ensure that the cluster environment meets these requirements:
- Include sufficient permissions in the vFXT IAM role for managing instances in multiple zones. In addition to the cluster controller permissions, each node must have the failover permissions
- Have an available CIDR range outside of the VPC CIDR range for the management, cluster, and client-facing addresses
- Configure routes for directing traffic to and from that additional CIDR range
- Ensure that clients can route to the client-facing addresses (a typical method is to have the EC2 instances share the same route table with the vFXT nodes)
The cluster itself is subject to the following limitations:
- The cluster can use a maximum of three Availability Zones.
- Each AZ can host only one vFXT node. (Using multiple zones limits the cluster to a size of three vFXT nodes.)
- Subnets must all be within the same VPC.
- All vFXT nodes should share the same route table.
Customizing the cluster node role¶
The vfxt.py script creates a role for the cluster nodes. You have the option to create your own role for cluster nodes and supply it to the vfxt.py script when you create the cluster.
The policy below is the default role assigned to vFXT nodes. If you use a custom role, make sure that it includes this information:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"ec2:AssignPrivateIpAddresses",
"ec2:UnassignPrivateIpAddresses",
"ec2:DescribeInstance*",
"ec2:DescribeRouteTables",
"ec2:DescribeSubnets",
"ec2:ReplaceRoute",
"ec2:CreateRoute",
"ec2:DeleteRoute"
],
"Resource": "*",
"Effect": "Allow"
}
]
}
Sample IAM policy¶
The following is the policy that should be cut and pasted to create the permissions for the cluster controller.
Click this link to download it as a text file: IAM policy
{
"Statement": [
{
"Resource": "*",
"Action": [
"ec2:Describe*",
"ec2:RunInstances",
"ec2:TerminateInstances",
"ec2:RebootInstances",
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:CreateTags",
"ec2:DeleteTags",
"ec2:ModifyInstanceAttribute",
"ec2:CreateVolume",
"ec2:DeleteVolume",
"ec2:AttachVolume",
"ec2:DetachVolume",
"ec2:CreateSnapshot",
"ec2:DeleteSnapshot",
"ec2:RegisterImage",
"ec2:DeregisterImage",
"ec2:CreateImage",
"ec2:DeleteRoute",
"s3:CreateBucket",
"s3:DeleteBucket",
"s3:SetTag",
"s3:ListBucket",
"iam:AddRoleToInstanceProfile",
"iam:CreateInstanceProfile",
"iam:CreateRole",
"iam:DeleteInstanceProfile",
"iam:DeleteRole",
"iam:DeleteRolePolicy",
"iam:GetRolePolicy",
"iam:ListRolePolicies",
"iam:GetInstanceProfile",
"iam:PutRolePolicy",
"iam:RemoveRoleFromInstanceProfile",
"iam:GetRole",
"iam:PassRole"
],
"Effect": "Allow"
}
],
"Version": "2012-04-18"
}
