kubernetes-hackfest
Delivering modern cloud-native applications with open source technologies on Azure Kubernetes Service
Module 5: Using alerts
Goal: Use global alerts to notify security and operations teams about unsanctioned or suspicious activity.
Steps
-
Review alerts manifests.
Navigate to
demo/50-alertsand review YAML manifests that represent alerts definitions. Each file contains an alert template and alert definition. Alerts templates can be used to quickly create an alert definition in the UI. -
View triggered alerts.
We implemented alerts in one of the first labs in order to see how our activity can trigger them.
kubectl get globalalertoutput will be like this:
NAME CREATED AT dns.unsanctioned.access 2021-06-10T03:24:41Z network.lateral.access 2021-06-10T03:24:43Z policy.globalnetworkset 2021-06-10T03:24:41ZOpen
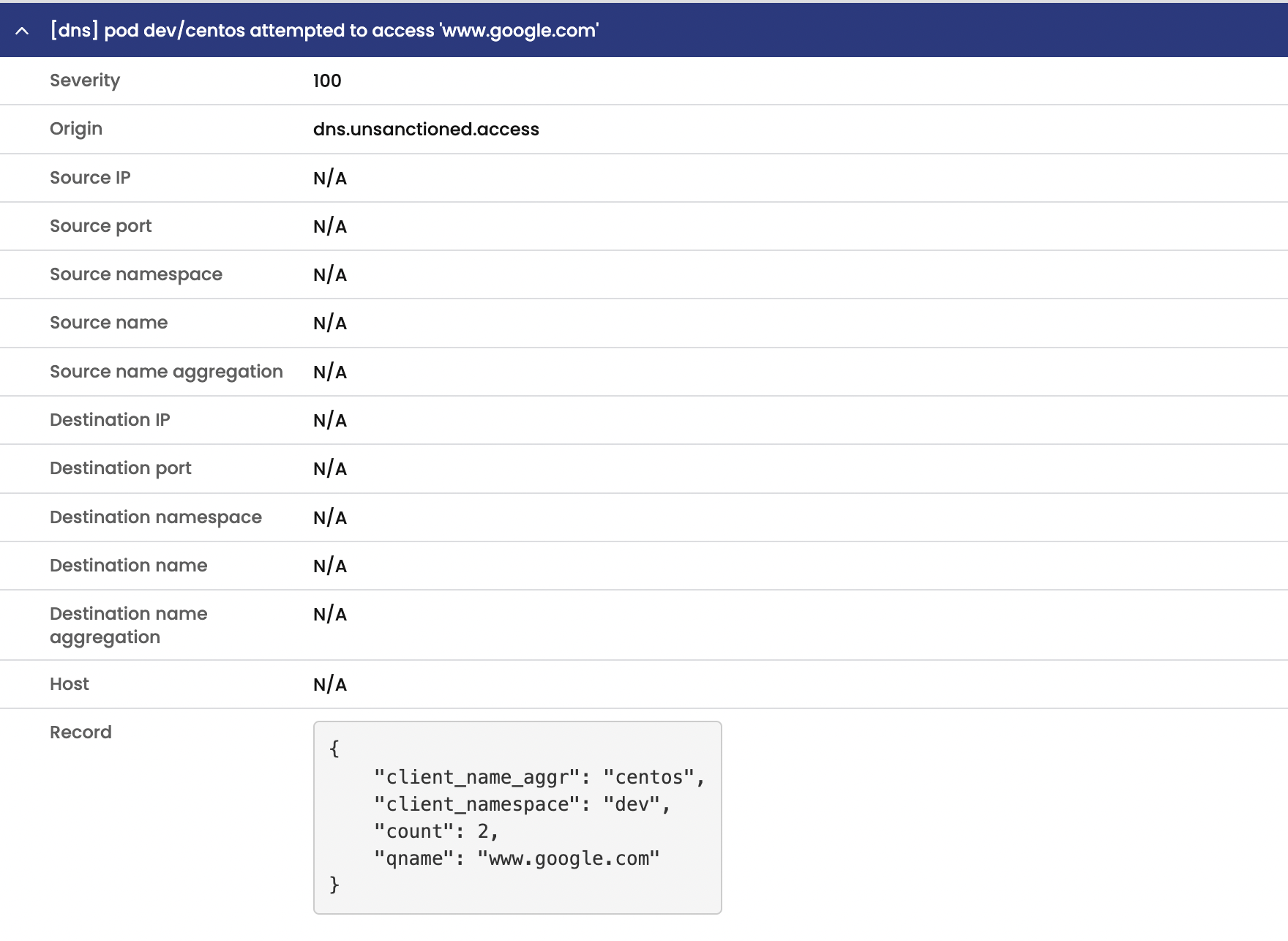
Alertsview to see all triggered alerts in the cluster. Review the generated alerts.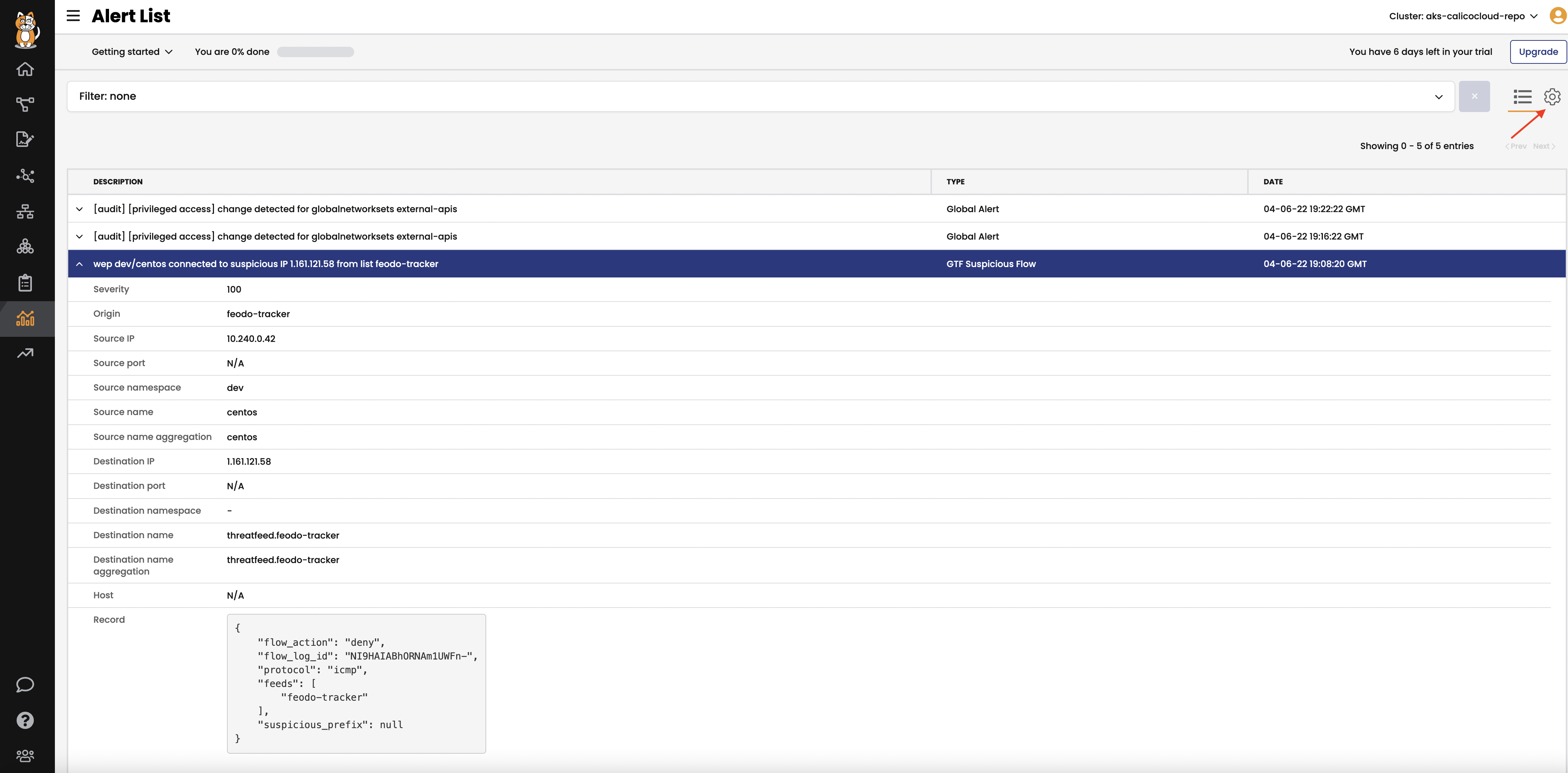
You can also review the alerts configuration and templates by navigating to alerts configuration in the top right corner.
-
Trigger dns alert by sending a curl request to www.google.com as defined in dns alert. Note: You need remove namespace
devfromdefault-denypolicy for trigger this alert, and it may take a minute or two to be visible in the ‘Alerts’ tab.kubectl -n dev exec -t centos -- sh -c 'curl -m3 -skI https://www.google.com 2>/dev/null | grep -i http'