Terraform Owner Contribution Flow
This section describes the contribution flow for module owners who are responsible for creating and maintaining Terraform Module repositories.
Important
This contribution flow is for Module owners only.
As a Terraform Module Owner you need to be aware of the AVM contribution process overview & Terraform specifications (including Interfaces) as as these need to be considered during pull request reviews for the modules you own.
Info
Make sure module authors/contributors tested their module in their environment before raising a PR. The PR uses e2e checks with 1ES agents in the 1ES subscriptions. At the moment their is no read access to the 1ES subscription. Also if more than two subscriptions are required for testing, that’s currently not supported.
1. Owner Activities and Responsibilities
Familiarise yourself with the responsibilities as Module Owner outlined in Team Definitions & RACI and in the TF Issue Triage.
- Watch Pull Request (PR) and issue (questions/feedback) activity for your module(s) in your repository and ensure that PRs are reviewed and merged in a timely manner as outlined in SNFR11.
Info
Make sure module authors/contributors tested their module in their environment before raising a PR. Also because once a PR is raised a e2e GitHib workflow pipeline is required to be run successfully before the PR can be merged. This is to ensure that the module is working as expected and is compliant with the AVM specifications.
2. GitHub repository creation and configuration
Once your module has been approved and you are ready to start development, you need to request that a new repository be created for your module.
You do that by adding a comment to the issue with the #RFRC tag. The Status: Ready For Repository Creation 📝 label will then be applied. This will trigger the creation of the repository and the configuration of the repository with the required settings.
Info
If you need your repository to be created urgently, please message the AVM Core team in the AVM Teams channel.
Once your module is ready for development, the Status: Repository Created 📄 label will be added to the issue and you’ll be notified it is ready.
3. Module Development Activities
You can now start developing your module, following standard guidance for Terraform module development.
Some useful things to know:
Pull Request
You can raise a pull request anytime, don’t wait until the end of the development cycle. Raise the PR after you first push your branch.
You can then use the PR to run end to end tests, check linting, etc.
Once readdy for review, you can request a review per step 4.
Grept
Grept is a linting tool for repositories, ensures predefined standards, maintains codebase consistency, and quality.
It’s using the grept configuration files from the Azure-Verified-Modules-Grept repository.
You can see here which files are synced from the terraform-azurerm-avm-template repository.
Set environment variables and run Grept:
export GITHUB_REPOSITORY_OWNER=Azure
export GITHUB_REPOSITORY=Azure/terraform-azurerm-avm-res-<RP>-<modulename>"
./avm grept-apply$env:GITHUB_REPOSITORY_OWNER="Azure"
$env:GITHUB_REPOSITORY="Azure/terraform-azurerm-avm-res-<RP>-<modulename>"
./avm grept-applyCustom Variables and Secrets for end to end tests
The respoitory has an environment called test, it has have approvals and secrets applied to it ready to run end to end tests.
- In the unusual cicumstance that you need to use your own tenant and subscription for end to end tests, you can override the secrets by setting
ARM_TENANT_ID_OVERRIDE,ARM_SUBSCRIPTION_ID_OVERRIDE, andARM_CLIENT_ID_OVERRIDEsecrets. - If you need to supply additional secrets or variables for your end to end tests, you can add them to the
testenvironment. They must be prefixed withTF_VAR_, otherwise they will be ignored.
4. Review the module
Once the development of the module has been completed, get the module reviewed from the AVM Core team by following the AVM Review of Terraform Modules process here which is a pre-requisite for the next step.
5. Publish the module
Once a module has been reviewed and the PR is merged to main. Follow the below steps to publish the module to the HashiCorp Registry.
Ensure your module is ready for publishing:
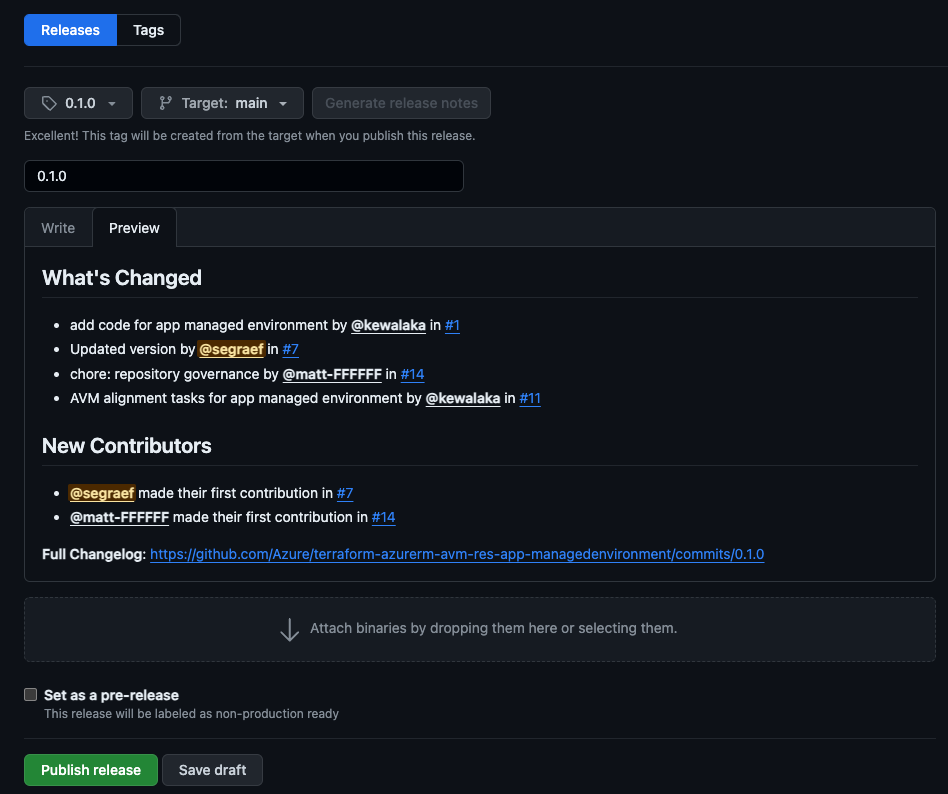
Create a release with a new tag (e.g.
0.1.0) via Github UI.- Go to the releases tab and click on
Draft a new release. - Ensure that the
Targetis set to themainbranch. - Select
Choose a tagand type in a new tag, such as0.1.0Make sure to create the tag from themainbranch. - Generate the release notes using the
Generate release notesbutton. - If this is a community contribution be sure to update the ‘Release Notes` to provide appropriate credit to the contributors.
- Go to the releases tab and click on
Elevate your respository access using the Open Source Management Portal.
Sign in to the HashiCorp Registry using GitHub.
Publish a module by selecting the
Publishbutton in the top right corner, thenModuleSelect the repository and accept the terms.
Info
Once a module gets updated and becomes a new version/release it will be automatically published with the latest published release version to the HashiCorp Registry.